Observations and Comments
We would like to congratulate TRAI on a well researched consultation paper, with refreshingly open points of view and well framed questions for consultation
We would respectfully like to draw the Authority’s attention to the following points of concern
- The paper focuses largely on urban and commercial use cases. It assumes WiFi to be a service that will be provided by commercial providers and consumed by users who are able to prove their identity on the basis of possession of a device or documentation.
- It does not take into account the fact that since the advent of smartphones, which are becoming more and more common in rural and semi-urban areas, even the average cellphone user can become a provider of data services simply by turning on the “WiFi HotSpot” functionality that is built into their phone. This sort of WiFi can be used both for peer to peer sharing of content as well as for providing secondary data access.
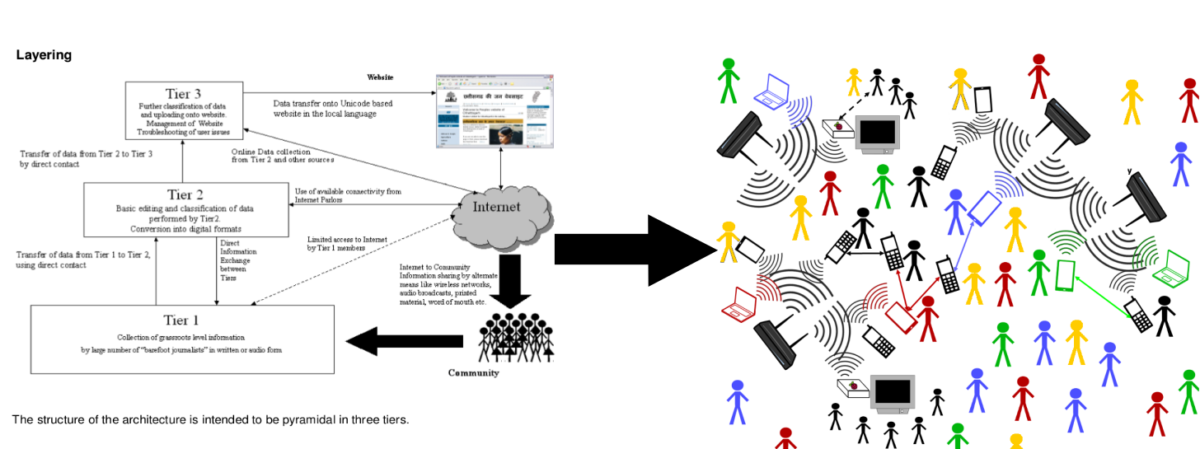
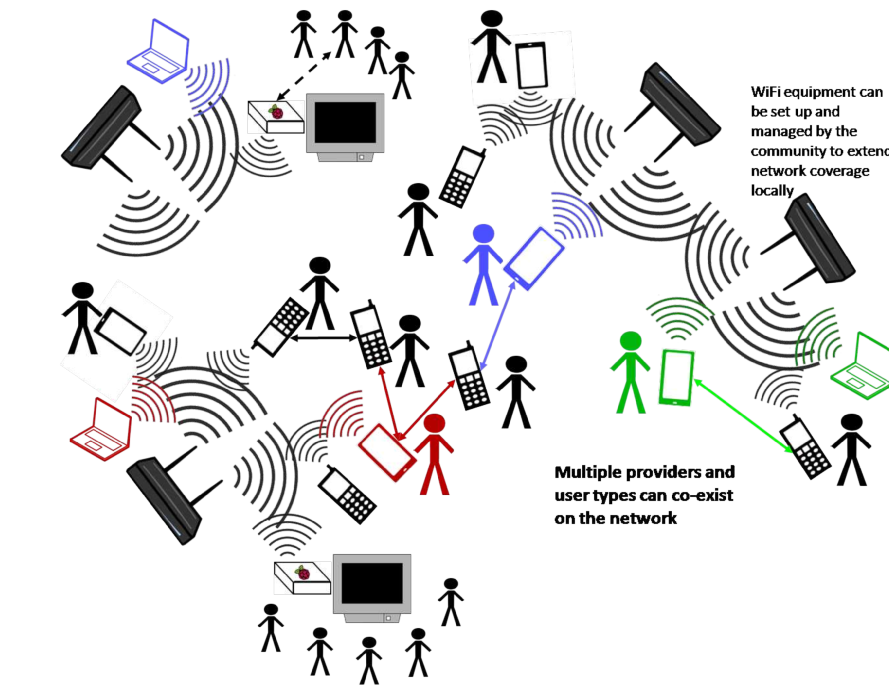
- Community owned and operated networks are also not covered either as a class by themselves or under another class. With WiFi equipment fast becoming easier to purchase even in rural and semi urban areas, more and more households are now purchasing WiFi equipment. This equipment can be interconnected by the community themselves to share data, communicate internally and also access full or limited connectivity to the Internet by pooling bandwidth and storing data locally. These networks can also be linked (in the future, when policy permits) to GSM networks to provide last mile cellphone connectivity even to remote rural areas. The COWMesh community is currently working on several pilot use-cases to establish feasibility and costs of providing different communication based services within and among communities.
e.g. COWMesh Ranikajal Kakrana (Madhya Pradesh), COWMesh Hale Kote (Karnataka), COWMesh Aruvikkara (Kerala)
A policy that allows communities to set up their own networks and possibly even gain acknowledgement and support for the same from the administration would be very welcome.
- Access Control –
- The issue of access control to data services is an important one. However, present mechanisms in place to verify identity online are not reliable.
- Given that technical competence in India is still in its developing stages, particularly in the grassroots, and given the strong social norms in place, password and other access details are often shared among multiple users. Rather than curb this natural behavior and encourage alienation in the family/community unit, why don’t we support community identities online
- Intra community agreements can be enforced by digital contract
- e.g. I change my password and give the changed password to a friend who is willing to sign a digital contract (via SMS, via app, via voice recording) and share liability for my account for the duration of the digital contract
- Upon expiry or termination of the contract, I change my password again
- The password changes can be managed by single sign on software to enable ease of use.
- If the model is kept suitably generic multiple mechanisms can be created to implement it
- Communities in India already impose internal standards, which are often followed more diligently than legal ones. By allowing communities to assume identities online on behalf of their members, this internal discipline can be utilized in the service of national security.
- While each individual member of a community may not have access to means of identification, every community will certainly have some members (or can incorporate new members) who have access to such means. These individuals can then become the digital stewards for their community and also be accountable for the communities online conduct. This is similar to the model of peer selected systems administrators for early networks that later coalesced to become the Internet as we know it today.
- We believe that the issue of online identification is a deeper one and should not be lumped in with the question of public WiFi beyond reasonable areas of overlap. A separate consultation by the appropriate authority on the subject of online identity would be very welcome.
- The paper does not adequately address the differential costs of data in different locations across the country and the significance of this phenomena in the proliferation of local WiFi networks. For example, the cost of data acquisition in a major city such as Bangalore is approximately INR 11 per GB @ 15Mbps (over broadband) whereas in rural MP, the same data costs approximately INR 100-250 per GB to download at 7.2Mbps (over 3G/4G), provided the network provides coverage in the area. Under these circumstances, it is actually feasible for individuals to download large volumes of content in locations where data is cheaply available and physically transport it for distribution in locations where it is not, either as a voluntary service or as a commercial one. By using low cost, easily available WiFi hardware, households can connect their television sets to each other and share content that has been downloaded once, thereby negating the need to download the same content again and again.The paper does capture this to some extent in point 2.22 and Table 2.4. However, the costs of infrastructure mentioned apply only to carrier grade commercial WiFi and not community owned/operated ones. The actual costs of infrastructure can be brought down significantly by adopting open source software and hardware.
- We fully support data sharing and reselling as described in section 3.25-3.27 (Fon example), provided that communities and individuals are allowed to participate.
- While discussing the possibility of linking WiFi to GSM networks, it is important to also note the policy in place that makes the setting up of PSTN to VoIP gateways illegal in India. If this policy can be reconsidered, WiFi can be used to also provide phone connectivity to rural areas that have not been connected so far.
Questions from TRAI for consultation and response
Q1. Are there any regulatory issues, licensing restrictions or other factors that are hampering the growth of public Wi-Fi services in the country?
TRAI itself in 2008 had issued some recommendations on restricting public wi-fi in the aftermath of the 2008 Mumbai terror attacks. After these recommendations, public wi-fi is linked to a cell phone number (sign-in/verification done via cell phone number). So perhaps there is a need to reframe public wifi not in terms of terrorism but perhaps as an extension of existing Broadband policy or universal access to information production, distribution and consumption or reception.
The cellphone number requirement also does not cover rural/community use cases adequately. For example, there is no policy coverage for the scenario where a group of households use their TVs to connect to a shared WiFi network, which hosts local content.
Re-framing in the context of access instead of security should work ground up, i.e. distinguish between different categories of public WiFi, e.g. i) complimentary WiFi provided by a commercial establishment to patrons/customers, ii) public internet access provided either commercially or pro bono to individuals who may register directly with the provider, iv) community owned and operated WiFi networks with limited or service based connectivity to the Internet and iii) non internet connected public wifi that provides access to “offline” downloaded content. Each would need to be considered separately and then a common policy framed with specific extensions to each category. Ideally, community owned and operated networks such as networks run by groups of individuals in small villages and apartment complexes in cities should be regulated only by the community operating them subject to the rules of the ISPs providing Internet connectivity to such networks.
Q2. What regulatory/licensing or policy measures are required to encourage the deployment of commercial models for ubiquitous city-wide Wi-Fi networks as well as expansion of Wi-Fi networks in remote or rural areas?
Bharat Broadband (BBNL) is a special purpose vehicle to implement country wide optic fibre network. This is public money to ensure internet connectivity to the public. Could public wi-fi be a part and extension of the BBNL mandate? If parts of this unlit pipe could be made available to community wifi networks, then it might be of great help. If we are to encourage ubiquitous city-wide Wi-Fi networks, then community based Wi-Fi mesh networks should be allowed (including but not limited to individuals who wish to share their home internet connection with others). It would also be helpful if WiFi equipment (transmitters, antenna, receivers etc.) could be exempt from import duties – as a move to encourage growth of ubiquitous public wifi.
Q3. What measures are required to encourage interoperability between the Wi-Fi networks of different service providers, both within the country and internationally?
We do not see an immediate concern regarding the interoperability of WiFi networks as the WiFi standard is is quite well defined and widely publicised. The concerns in this area appear to be around seamless roaming and unified payment. We believe that imposing more standardisation at this time would serve only the urban elite users of WiFi networks by providing some minor conveniences, but the resulting increase in baseline cost of compliance will prevent smaller players from participating effectively. Therefore at this time we do not suggest any more measures to encourage interoperability, beyond conforming to the WiFi hardware and broadcasting standards.
However, as the medium becomes more popular, it would be useful to encourage mechanisms that allow individual and community owned WiFi networks to partner with existing ISPs to provide multipath internet connectivity.
Q4.What measures are required to encourage interoperability between cellular and Wi-Fi networks?
The policy in India regarding GSM has been quite restrictive so far. Many open source and low cost platforms such as Software Defined Radio (SDR) and OpenBTS are being developed internationally the availability of which for research purposes would allow more people to use cellular technology. However these developments often take more than the expected time to reach India due to trade and policy restrictions. If these regulations can be eased up, then new links can be explored along the lines of Rhizomatica in Mexico.
Q5.Apart from frequency bands already recommended by TRAI and DoT, are there additional bands which need to be de-licensed in order to expedite the penetration of broadband using Wifi technology?
Please provide international examples, if any, in support of your answer.
There is of course 2.4 GHz already reserved for Wi-Fi, but if we see long term possibilities, then TRAI needs to consider developing hardware and software ecology around 5 GHz as well. Further, the government has earned a lot of revenue from 700 MHz for 4G networks via auctions and bidding by telecom operators. So a part of that revenue could be used to provide free and public wi-fi.
Q6. Are there any challenges being faced in the login/authentication procedure for access to Wi-Fi hotspots? In what ways can the process be simplified to provide frictionless access to public Wi-Fi hotspots, for domestic users as well as foreign tourists?
As described above in the observations as well as the answer to Question 1, linking of public WiFi access to mobile phone numbers is restrictive on users and inadequate from a security point of view. Alternative methods of verification could be used. Perhaps a coupon system, where authorized access providers register via mobile phone and then are authorized to allow other users on to the network based on a set of coupons linked to the access providers ID. So all users are still associated to one phone number or the other, but even people without cellphones or electronic payment methods can participate.
We should avoid making public WiFi access dependent on cellphone ownership or infrastructure to generate OTPs or access to electronic payment mechanisms.
Q7. Are there any challenges being faced in making payments for access to Wi-Fi hotspots? Please elaborate and suggest a payment arrangement which will offer frictionless and secured payment for the access of Wi-Fi services.
It is difficult for cash users and users without electronic payment options to use public WiFi. The coupon system would resolve this as well. This is important to ensure proliferation of WiFi services in rural and semi urban areas. There are two many different scenarios in which WiFi access may be paid for to assume that a unified payment model will work for all of them. In the case of WiFi services, there are two kinds of access that a user will always have to pay for. One is the access to the medium itself, which is controlled by the entity who owns the equipment to which the user is connecting. This is a local transaction and is not dependent on electronic means as the user and the service provider are in the same location. The second question is the question of access to the Internet while connected to the WiFi. The Internet services may not be provided to all users on a WiFi network and may be controlled based on role or payment.
In either case, any provider who has the technical competence to set up a restricted access network with connectivity to the Internet should also be expected to set up a viable payment gateway so as not to inconvenience the user. The current model allows the equipment owner to choose in what manner to allow users access, whereas mandating a centralized payment standard may not. In our opinion there is no need for policy intervention on this matter.
Q8.Is there a need to adopt a hub-based model along the lines suggested by the WBA, where a central third party AAA (Authentication, Authorization and Accounting) hub will facilitate interconnection, authentication and payments? Who should own and control the hub? Should the hub operator be subject to any regulations to ensure service standards, data protection, etc?
More centralization should certainly not be encouraged as it slows down adoption if the central agency has to be approached by each provider and is particularly detrimental to smaller providers. Instead each network should be allowed to manage its own authentication and work out partner agreements with other networks to facilitate roaming between partner networks. This way smaller operators can partner with larger ones or amongst themselves to extend connectivity, rather than needing to go to a central authority for each agreement. Payment between operators should be left out of the purview of wifi regulation as it falls in the category of electronic payments which is independently being dealt with by different laws (RBI/SEBI)
For authentication, a distributed model is needed. Multiple aggregation services should be encouraged to syndicate authentication and user data between networks rather than maintaining one central system.
Q9.Is there a need for ISPs/ the proposed hub operator to adopt the Unified Payment Interface (UPI) or other similar payment platforms for easy subscription of Wi-Fi access? Who should own and control such payment platforms? Please give full details in support of your answer.
Access to/ adoption of the UPI should be optional and not mandatory. Inclusion of UPI as a payment option is welcome provided there are multiple options and that options are not excluded in order to include UPI. It should not be assumed that WiFi networks will only be operated by ISPs. Communities and individuals may also operate networks. If a mandate is imposed, it will negatively impact the ability of local providers to compete. Currently they have a stronger market position in rural areas since telecom infrastructure extension is not cost feasible for operators. Therefore local operators should be encouraged by providing benefits to the smaller players rather than mandates that benefit the existing corporations. Payment for WiFi access, if needed, must be made through the owner of the equipment. This allows the owner of the equipment to control the mode of access and sharing of data, which is essential as the liability for any misuse of the equipment by the users is also borne by the owner of the equipment.
If a centralized payment platform is mandated, this may hamper the ability of the equipment owner to control access. Further, not all public WiFi networks may be connected to the Internet. Local networks are possible where content is hosted by a community, an individual or a commercial provider for which they may choose to charge a fee. A centralized payment mechanism mandate excludes this use case and other similar ones.
Q10. Is it feasible to have an architecture wherein a common grid can be created through which any small entity can become a data service provider and able to share its available data to any consumer or user?
Yes, given that even smartphones today can be used to create local small range WiFi networks and low cost computing devices such as Raspberry Pi are available to act as servers, even a village household can become a data service provider by simply taking a smartphone to a connected zone, downloading some content and bringing it back to the village to share with other friends over WiFi. Existing data connections on the phone can also be shared via the WiFi hotspot option on Android phones.
Given this ability, we should make it viable for people to start tracking and benefiting from the data that they deliver. Perhaps in the future blockchain and similar technologies will help track data transfers and reduce the duplication in the transfer of content.
Q11. What regulatory/licensing measures are required to develop such architecture? Is this a right time to allow such reselling of data to ensure affordable data tariff to public, ensure ubiquitous presence of Wi-Fi Network and allow innovation in the market?
Any regulatory measures that are taken should be taken towards promoting reselling of data. It is important here to distinguish the term data into two components i.e. bandwidth and content. Individuals, communities and small businesses should all be allowed to resell both bandwidth and content. For example, a cellphone owner who downloads a video (which he is entitled to download, i.e. a non copyright video) is already allowed to use the WiFi HotSpot functionality of his phone to reshare that content with multiple users. This is sharing of content. However, the same device can also be used to provide direct access to the internet by multiple users.
This would qualify as sharing of bandwidth.
In this case, the liability for access rests on the user providing the hotspot, and there is no way to transfer that liability to the actual user by accepting payment for value of connectivity service rendered by contract (i.e. resale of data services).
The same applies to owners of home WiFi equipment who have unused bandwidth that they could resell. For example, many urban households have broadband connections with fair use limits far above their own consumption. If they could resell this excess connectivity and devolve the liability from the use of said connectivity by accepting payment via contract, this would help increase household incomes as well as bring more affordable connectivity to the masses.
If this can be encouraged, individuals, communities and businesses would be able to develop more effective ways to get information to remote locations by re-trading both bandwidth as well as content in the most efficient way possible.
Q12. What measures are required to promote hosting of data of community interest at local level to reduce cost of data to the consumers?
There are now several free and open source platforms that allow communities to host content offline, such as WordPress (text and multimedia), Kolibri (educational content), ClipBucket (video hosting) and so on. These platforms can be hosted on user level devices such as laptops and single board computing systems such as RaspberryPi which can also be used to connect regular CRT television sets to the WiFi network.
The television is a device that stays within the household and accessible to women and children, as opposed to smartphones which are usually owned and almost exclusively operated by the man of the house. The goal of connecting households rather than individuals can be well supported by the local hosting model.
In order for full utilization of community resources and to maintain participation, community members should be encouraged to host local content and share/provide access to their neighbours. This model can be used to promote good quality independent content in addition to commercially made content at the grassroots level.
Q13. Any other issue related to the matter of Consultation
Respondents
- Arjun Venkatraman, The Mojolab Foundation, arjun@mojolab.org
- Ram Bhat, Maraa, ram@maraa.in
- Rahul Bannerji, DHAS Grameen Vikas Kendra, Khedut Mazdoor Chetna Sangathan, rahul.indauri@gmail.com
- Swapan Bhattacharjee, Ex BARC Scientific Officer, Guest adviser to RaniKajal Jeevan Shala, Kakrana, swapan1943@gmail.com
- The COWMesh Ranikajal Community, Kakrana, Madhya Pradesh, cowmail.ranikajal@gmail.com
 The
The  As a result, the local population get precious few nutrients and those usually from animal sources such as reared goats, hardy animals that can increase muscle weight even on a diet of scrub grass, and fish.
As a result, the local population get precious few nutrients and those usually from animal sources such as reared goats, hardy animals that can increase muscle weight even on a diet of scrub grass, and fish.

 The Internet is fast establishing itself as the central nervous system of a newly evolving entity, i.e. connected humanity. For the first time in the history of our planet, a species has built a mechanism that allows members displaced over great distances to communicate instantly, using electricity as the medium. This is no smaller feat than the evolution of the central nervous system in life forms on this planet, which is the basis of identity and self awareness.
The Internet is fast establishing itself as the central nervous system of a newly evolving entity, i.e. connected humanity. For the first time in the history of our planet, a species has built a mechanism that allows members displaced over great distances to communicate instantly, using electricity as the medium. This is no smaller feat than the evolution of the central nervous system in life forms on this planet, which is the basis of identity and self awareness. find it worthwhile to buy, own and operate a network of their own. We explored many groups, ranging from urban low income housing communities in Bangalore, to elite IIT-JEE training facilities in rural Maharashtra to members of both the tourism industry and the development community in Uttarakhand, but we were unable to establish a usecase for any of the communities that warranted expense and effort by the community themselves. It seemed that those disenfranchised by the telecommunications industry had given up hope.
find it worthwhile to buy, own and operate a network of their own. We explored many groups, ranging from urban low income housing communities in Bangalore, to elite IIT-JEE training facilities in rural Maharashtra to members of both the tourism industry and the development community in Uttarakhand, but we were unable to establish a usecase for any of the communities that warranted expense and effort by the community themselves. It seemed that those disenfranchised by the telecommunications industry had given up hope. Finally in October of 2015, we had a communication from Indore, from Shri
Finally in October of 2015, we had a communication from Indore, from Shri  irajpur.
irajpur.